Advanced Zero-Day Attack Detection Honeypot System with Real-Time Threat Intelligence Dashboard
Enterprise-grade honeypot monitoring system that simulates vulnerable network services to detect zero-day attacks, malware patterns, and cyber threats in real-time with GeoIP tracking, automated threat scoring, and comprehensive security analytics.
Technology Used
Django 5.0 | Python 3.10 | Django Channels | Redis | WebSockets | Celery | SQLite | PostgreSQL | Chart.js | Leaflet.js | Three.js | GeoIP2 | Asyncio | HTML5 | CSS3 | JavaScript | Bootstrap
Project Files
Advanced Honeypot System for Zero-Day Attack Analysis and Threat Detection
Deploy a professional-grade cybersecurity honeypot system designed to attract, analyze, and document sophisticated cyber attacks including zero-day exploits. This comprehensive Django-based security monitoring platform provides real-time threat intelligence, attack pattern recognition, and detailed forensic analysis capabilities essential for modern network defense strategies.
Core Project Features
- Multi-Protocol Attack Simulation: Emulates vulnerable SSH, FTP, HTTP, Telnet, and SMB services to create realistic attack surfaces that attract malicious actors while maintaining complete system isolation and security
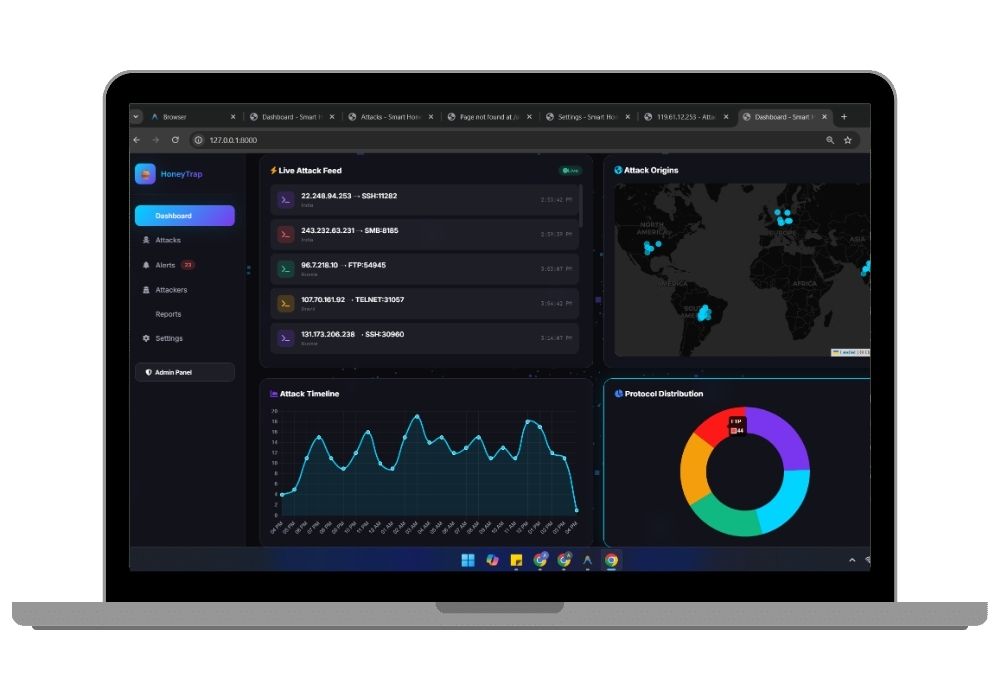
- Real-Time Attack Monitoring Dashboard: WebSocket-powered live feed displays incoming attacks instantly with protocol distribution analytics, attack timeline visualization, and threat severity indicators
- Interactive 3D GeoIP Visualization: Dynamic world map integration using Leaflet.js and Three.js renders attack origins geographically with real-time marker updates showing global threat patterns
- Intelligent Threat Scoring Engine: Automated analysis system calculates threat levels based on attack frequency, command patterns, malware signatures, and behavioral anomalies using machine learning
- Advanced Security Controls: Built-in IP blacklisting, rate limiting mechanisms, honeypot isolation protocols, and automated response systems prevent lateral network movement
- Comprehensive Reporting Suite: Generate executive summaries, export attack logs in CSV/JSON/PDF formats, and create detailed forensic reports for security audits
- Attacker Profiling System: Tracks individual threat actors across sessions, building comprehensive profiles with activity history, geographic data, and threat intelligence scores
- Pattern Detection Algorithms: Machine learning-powered anomaly detection identifies zero-day exploitation attempts, SQL injection patterns, and emerging attack vectors
Technical Architecture and Implementation
Built on Django 5.0 framework with Python 3.10, the system leverages asynchronous programming for handling multiple concurrent connections across simulated services. Django Channels with Redis backend enables real-time WebSocket communication for instant dashboard updates. The glassmorphic dark-mode interface provides intuitive security analytics visualization while maintaining professional aesthetics suitable for SOC environments. Similar to our Website Vulnerability Scanner, this project demonstrates advanced security monitoring capabilities.
Real-World Applications
- Cybersecurity Research: Academic institutions studying attack methodologies, malware propagation patterns, and threat actor behavior in controlled environments
- Network Security Operations: Enterprise SOC teams deploying early warning systems to detect reconnaissance activities and potential intrusion attempts, similar to our Hierarchical Intrusion Detection System
- Penetration Testing: Security professionals testing defensive capabilities and training incident response teams with realistic attack scenarios, complementing tools like our VulnHunt Bug Bounty Platform
- Threat Intelligence Gathering: Organizations collecting indicators of compromise (IOCs), malware samples, and attack signatures for threat databases
- Security Training and Education: Universities and training centers providing hands-on experience with real-world attack patterns and defensive technologies
- Compliance and Audit: Meeting regulatory requirements for intrusion detection systems and security monitoring infrastructure
Advanced Security Features
The honeypot system implements multiple layers of protection ensuring the monitoring infrastructure itself remains secure. Network isolation prevents attackers from pivoting to production systems. Rate limiting and automatic blacklisting block aggressive scanning activities. All captured data undergoes encryption before storage, utilizing techniques similar to our Image Steganography project. The system maintains detailed audit logs suitable for forensic investigation and compliance reporting.
Data Analytics and Visualization
Powered by Chart.js for statistical visualizations, the dashboard presents attack data through multiple lenses including temporal analysis, geographic distribution, protocol breakdown, and threat severity metrics. Custom algorithms identify attack campaigns by correlating multiple indicators across time periods. Export functionality enables integration with external SIEM platforms and threat intelligence feeds, similar to our Crime Data Visualization Tool.
Scalability and Deployment
Designed for deployment on isolated virtual machines, VPS hosting, or DMZ network segments. Supports PostgreSQL for production environments handling high-volume attack data. Celery integration enables distributed processing for complex analysis tasks. Docker containerization available for rapid deployment and horizontal scaling across multiple honeypot nodes. For assistance with deployment, check our project setup services.
Why Choose This Final Year Project
This honeypot system represents cutting-edge cybersecurity technology combining network programming, real-time data processing, machine learning for threat detection, and advanced web development. Students gain practical experience with security concepts, asynchronous programming, WebSocket communication, geospatial data visualization, and enterprise-grade system architecture. The project demonstrates mastery of multiple complex domains essential for modern cybersecurity careers. Browse more final year projects or explore our complete cybersecurity project collection.
Project Deliverables
- Complete Django-based honeypot system with multi-protocol simulation capabilities
- Real-time monitoring dashboard with WebSocket integration and glassmorphic UI design
- Comprehensive documentation covering installation, configuration, and operational procedures
- Pre-populated demonstration data for immediate testing and presentation purposes
- Attack simulation scripts for validating system functionality without real threats
- Detailed project report explaining architecture, algorithms, and security implementation
- Research paper draft suitable for academic publication - learn more about our research paper publication services
- PowerPoint presentation with technical diagrams and demonstration screenshots
Learning Outcomes
Students completing this project will master advanced Python programming including asyncio for concurrent operations, Django framework architecture for complex web applications, WebSocket protocols for real-time communication, security concepts including threat modeling and attack surface analysis, data visualization techniques using modern JavaScript libraries, and database design for high-volume security data storage and analysis. Need guidance? Explore our mentorship program or check our success stories from students who completed similar projects.
Related Projects
If you're interested in cybersecurity projects, you might also like our Phishing Website Detection, PhishGuard AI Email Detection, KeyDefender Keylogger Detection, AI-Based Malware Detection, and WiFi Packet Sniffer with 3D Visualization. For all available options, visit our projects page or use our project finder tool.
Extra Add-Ons Available – Elevate Your Project
Add any of these professional upgrades to save time and impress your evaluators.
Project Setup
We'll install and configure the project on your PC via remote session (Google Meet, Zoom, or AnyDesk).
Source Code Explanation
1-hour live session to explain logic, flow, database design, and key features.
Want to know exactly how the setup works? Review our detailed step-by-step process before scheduling your session.
₹999
Custom Documents (College-Tailored)
- Custom Project Report: ₹1,200
- Custom Research Paper: ₹1000
- Custom PPT: ₹500
Fully customized to match your college format, guidelines, and submission standards.
Project Modification
Need feature changes, UI updates, or new features added?
Charges vary based on complexity.
We'll review your request and provide a clear quote before starting work.

