KeyDefender - AI-Powered Keylogger Detection & Real-Time System Protection | Python Django Final Year Project
Advanced cybersecurity final year project with Django that detects keyloggers in real-time using behavioral analysis, heuristic algorithms, and process monitoring. Complete source code, documentation, and setup support included.
Technology Used
Python 3.8+ | Django 4.2.7 | psutil 5.9.6 | pywin32 306 | SQLite | HTML5 | CSS3 | JavaScript ES6+ | Chart.js | Font Awesome 6.4.0 | AJAX | JSON
Project Files
🛡️ KeyDefender - Professional Keylogger Detection System for Final Year Projects
KeyDefender is a production-ready cybersecurity application built with Python Django framework that provides real-time protection against keyloggers, spyware, and malicious processes attempting to steal sensitive information like passwords, banking details, and personal data. This comprehensive final year project combines advanced behavioral analysis with modern web technologies to create an enterprise-grade security solution.
🎯 Perfect For Your Final Year Project
- Computer Science Engineering (CSE) - Advanced software development with security focus
- Information Technology (IT) - Cybersecurity and system protection implementation
- Cyber Security Specialization - Real-world threat detection and mitigation
- Software Engineering - Full-stack web application with complex backend logic
✨ Advanced Project Features
🔍 Real-Time Process Monitoring
Continuously scans all running system processes using psutil library with cross-platform compatibility for Windows, Linux, and macOS. Monitors over 150+ process attributes in real-time.
🧠 Behavioral Analysis Engine
Advanced heuristic algorithms analyze suspicious patterns including keyboard hooks, hidden file access, abnormal CPU usage, network connections, and parent-child process relationships for accurate threat detection.
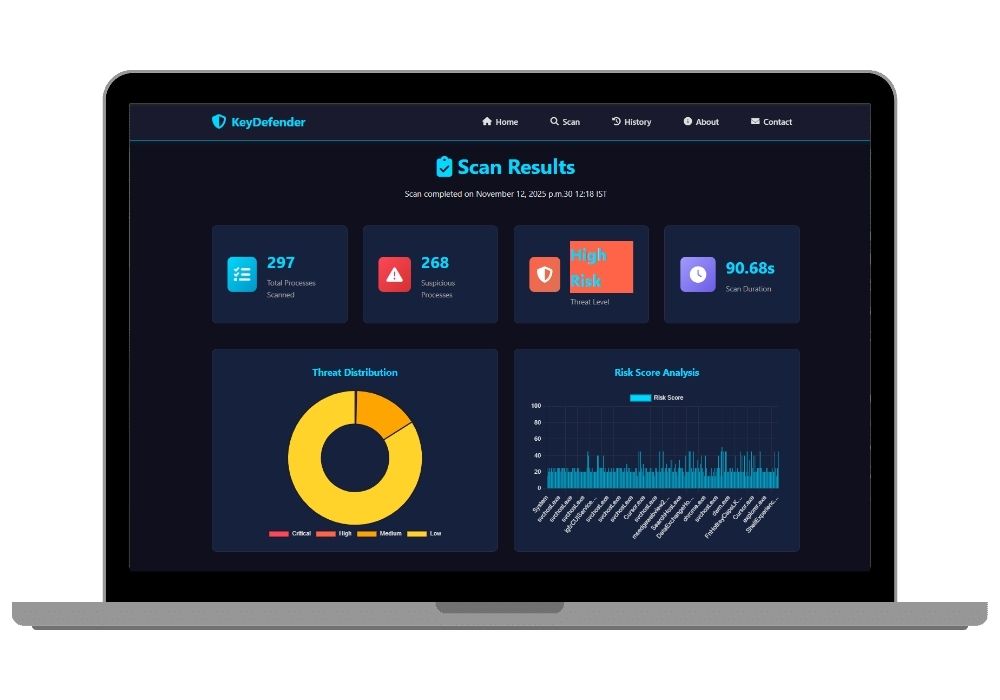
📊 Multi-Factor Risk Scoring System
Sophisticated scoring algorithm assigns risk levels (0-100) based on 8+ threat indicators with weighted calculations. Automatically classifies threats into Critical, High, Medium, Low, and Safe categories.
⚡ Instant Process Termination
One-click malicious process termination with admin privilege handling. Prevents data theft by immediately stopping suspicious activities before damage occurs.
📜 Comprehensive Audit Trail
Complete scan history with SQLite database storage. Track all detection events with timestamps, threat levels, process details, and historical trend analysis.
📈 Interactive Visual Analytics
Beautiful data visualization using Chart.js library. Pie charts for threat distribution, line graphs for historical trends, and bar charts for risk score analysis.
🎨 Modern Cybersecurity UI/UX
Responsive dark-themed interface with navy/blue color scheme and cyan accents. Professional design works seamlessly on desktop, tablet, and mobile devices.
🔐 Multi-Layer Detection Capabilities
Pattern matching for suspicious process names, hidden directory analysis, keyboard hook monitoring, log file access detection, long-running process identification, and network behavior analysis.
🚀 Real-World Applications
- Personal Computer Security: Protect home computers from spyware and keyloggers installed by malicious software or unauthorized users
- Corporate IT Security: Enterprise-level workstation monitoring for companies to prevent data breaches and insider threats
- Educational Institutions: Secure computer labs and student systems from unauthorized monitoring software
- Banking & Financial Sector: Additional security layer to protect sensitive financial data entry points
- Government Organizations: Detect espionage attempts and unauthorized surveillance software on classified systems
- Cyber Cafes & Shared Computers: Ensure customer privacy by detecting hidden monitoring tools
- Remote Work Security: Protect work-from-home setups from sophisticated spyware attacks
- Penetration Testing: Security researchers can use it to verify system integrity during audits
💼 Industry-Relevant Technology Stack
Backend Framework: Django 4.2.7 - Industry-standard Python web framework with MVC architecture, ORM, built-in admin panel, and security features
Process Monitoring: psutil 5.9.6 - Cross-platform library for system and process monitoring with low overhead
Windows Integration: pywin32 306 - Advanced Windows API access for deep system-level operations
Database: SQLite (included) with easy migration path to PostgreSQL or MySQL for production
Frontend: HTML5, CSS3, JavaScript ES6+ with AJAX for dynamic updates without page refresh
Data Visualization: Chart.js - Responsive, interactive charts with beautiful animations
Icons & UI: Font Awesome 6.4.0 - Professional icon library with 1000+ icons
🎓 Academic Excellence Features
- Well-Documented Codebase: Every function and class includes detailed comments explaining logic and algorithms
- MVC Architecture: Clean separation of concerns following Django best practices for maintainability
- Research-Backed Approach: Detection algorithms based on published cybersecurity research papers
- Scalable Design: Modular structure allows easy addition of new detection methods
- Security Best Practices: CSRF protection, SQL injection prevention, XSS filtering, secure session management
- Performance Optimized: Efficient database queries, minimal resource consumption, fast scan completion
📦 What You Get With This Project
- ✅ Complete Source Code - Fully functional Django application with all files and dependencies
- ✅ SQLite Database - Pre-configured database schema with sample data for testing
- ✅ Installation Guide - Step-by-step setup instructions for Windows, Linux, and macOS
- ✅ Requirements.txt - All Python dependencies with exact versions for easy installation
- ✅ Detailed README - 5000+ word documentation covering features, usage, and troubleshooting
- ✅ Code Comments - Line-by-line explanations of complex algorithms and logic
- ✅ Admin Panel - Pre-configured Django admin for database management
- ✅ Responsive Templates - 6 professionally designed HTML pages (Home, Scan, Results, History, About, Contact)
- ✅ Custom CSS & JavaScript - Cybersecurity-themed styling and interactive features
- ✅ Free Lifetime Updates - Get bug fixes and feature enhancements at no extra cost
🎯 Ideal for Multiple Project Types
- B.Tech / BE Final Year Projects
- MCA / M.Tech Dissertation Projects
- Computer Science Capstone Projects
- Cybersecurity Course Projects
- Web Development Portfolio Projects
- Research Paper Implementation Projects
⚡ Quick Setup - Ready in 15 Minutes
Unlike complex projects requiring days of setup, KeyDefender is designed for quick deployment. Follow our comprehensive installation guide to get your project running in just 15 minutes. No prior Django experience required - perfect for students learning web development.
🏆 Why Choose KeyDefender for Your Final Year Project?
- Unique & Trending Topic: Cybersecurity is one of the most in-demand fields with high industry relevance
- Impressive Demonstration: Real-time threat detection creates wow factor during project presentations
- Strong Academic Foundation: Based on documented algorithms and security research methodologies
- Industry-Ready Code: Professional coding standards that showcase your software engineering skills
- Easy to Explain: Clear architecture and well-commented code make viva voce questions manageable
- Extension Possibilities: Multiple ways to add features for higher marks (ML integration, cloud deployment, mobile app)
💡 Possible Project Extensions & Enhancements
Take your project to the next level with these additional features:
- Machine Learning classifier for improved detection accuracy using scikit-learn
- Email/SMS alerts for critical threats using Twilio or SendGrid APIs
- Cloud deployment on AWS, Azure, or Heroku with CI/CD pipeline
- Scheduled automatic scans using Celery task queue
- User authentication and multi-user support with role-based access
- Export reports to PDF using ReportLab or WeasyPrint
- Integration with antivirus APIs for enhanced detection
- Mobile app companion using Flutter or React Native
🎓 Perfect Documentation for Academic Submission
Our project includes everything needed for academic documentation: system architecture diagrams, flowcharts, use case diagrams, ER diagrams, algorithm pseudocode, test cases, and screenshots. Save weeks of documentation time!
📞 Comprehensive Support & Guidance
Unlike other project sellers, we provide ongoing support through CodeAj's dedicated support team. Get help with installation issues, code explanations, feature additions, and viva preparation tips.
🔒 100% Original & Plagiarism-Free Code
All code is written from scratch by experienced developers. No copied or template-based code. Safe for university submission with anti-plagiarism software.
Extra Add-Ons Available – Elevate Your Project
Add any of these professional upgrades to save time and impress your evaluators.
Project Setup
We'll install and configure the project on your PC via remote session (Google Meet, Zoom, or AnyDesk).
Source Code Explanation
1-hour live session to explain logic, flow, database design, and key features.
Want to know exactly how the setup works? Review our detailed step-by-step process before scheduling your session.
₹999
Custom Documents (College-Tailored)
- Custom Project Report: ₹1,200
- Custom Research Paper: ₹1000
- Custom PPT: ₹500
Fully customized to match your college format, guidelines, and submission standards.
Project Modification
Need feature changes, UI updates, or new features added?
Charges vary based on complexity.
We'll review your request and provide a clear quote before starting work.

