Advanced Network Security Vulnerability Scanner & Penetration Testing Platform with Real-Time Monitoring
Professional-grade Django-based network vulnerability assessment platform with automated port scanning, CVE detection, service enumeration, and comprehensive PDF reporting system for cybersecurity final year projects.
Technology Used
Django 4.2 | Python 3.8+ | Celery | Redis | python-nmap | PostgreSQL | ReportLab | Bootstrap 5 | Chart.js | JavaScript | NVD API | HTML5 | CSS3
Project Files
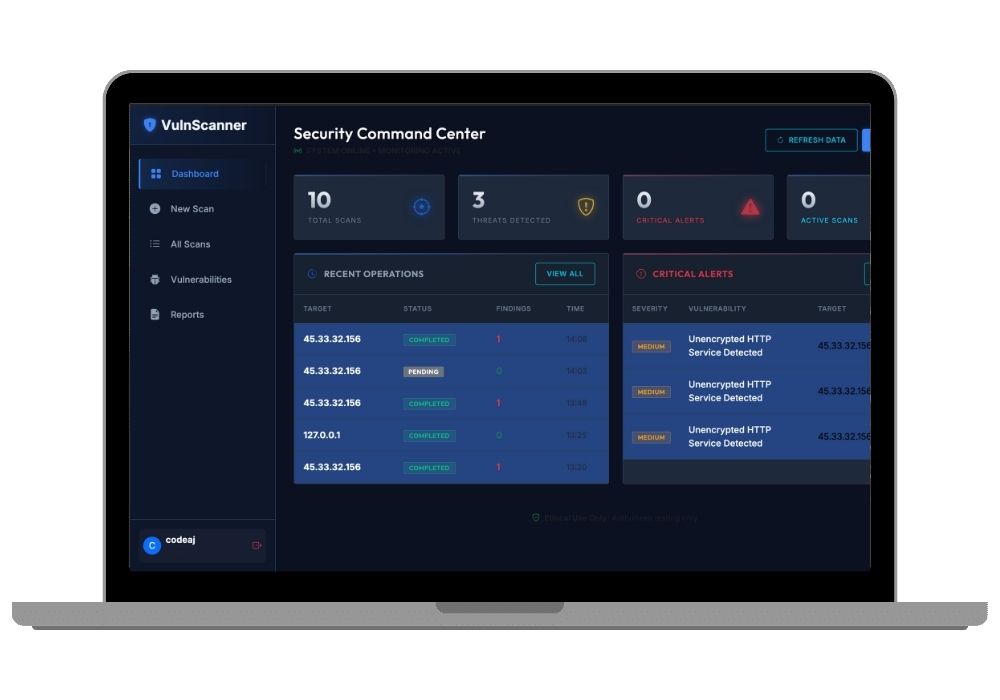
Complete Network Vulnerability Testing Platform for Final Year Project
This comprehensive network security assessment platform is an ideal final year project for computer science and cybersecurity students. Built with Django and advanced security tools, this project demonstrates professional-level penetration testing capabilities with real-time monitoring and detailed vulnerability reporting.
Project Overview
The Network Vulnerabilities Testing Website is a full-stack web application designed to identify, analyze, and report security vulnerabilities in network infrastructure. This project combines modern web technologies with industry-standard security scanning tools to create a powerful cybersecurity assessment platform suitable for academic projects and professional portfolio development.
Key Features of the Vulnerability Scanner
1. Comprehensive Port Scanning Capabilities
The system integrates python-nmap to perform advanced TCP and UDP port scanning across network ranges. Students can scan individual hosts or entire subnets to identify open ports, which is the first step in any security assessment. The scanner supports multiple scanning techniques including SYN stealth scans, connect scans, and UDP scans.
2. Service and Version Detection
Beyond simple port identification, the platform performs service enumeration to detect running services and their versions. This feature helps identify potentially vulnerable services by matching detected versions against known vulnerability databases. The service detection module can identify web servers, database systems, mail servers, and other network services.
3. Automated Vulnerability Detection Engine
The core vulnerability detection system analyzes scan results to identify common security misconfigurations and weaknesses. It checks for outdated software versions, default credentials, unnecessary open ports, and other security issues. The detection engine is extensible, allowing students to add custom vulnerability checks.
4. CVE Database Integration
Integration with the National Vulnerability Database provides access to thousands of known Common Vulnerabilities and Exposures. When a service version is detected, the system automatically queries the NVD API to retrieve relevant CVE entries, severity scores, and remediation recommendations.
5. Real-Time Progress Tracking System
Using Celery and Redis, the platform provides live updates during scanning operations. Users can monitor scan progress through a dynamic web interface that displays current scanning status, discovered hosts, open ports, and detected vulnerabilities as they are found. This asynchronous task processing ensures the web interface remains responsive during long-running scans.
6. Professional Report Generation
The reporting module generates comprehensive security assessment reports in multiple formats including PDF, CSV, and JSON. PDF reports include executive summaries, detailed vulnerability listings with CVSS scores, remediation recommendations, and visual charts. These reports follow industry standards and can be used for academic presentations or professional documentation.
7. Role-Based Access Control
The platform implements a sophisticated user management system with three distinct roles: Administrators who can manage users and system settings, Analysts who can create and run scans, and Viewers who can only review results. This multi-tier access control demonstrates understanding of secure application design principles, similar to our hostel management system.
8. Complete Audit Logging
Every security scanning activity is logged with timestamps, user information, and scan parameters. This audit trail is essential for compliance and forensic analysis. The logging system demonstrates implementation of security best practices and accountability mechanisms.
9. Responsive Modern Interface
Built with Bootstrap 5 and modern JavaScript, the user interface is fully responsive and works seamlessly across desktop, tablet, and mobile devices. The dashboard includes interactive charts powered by Chart.js to visualize vulnerability distributions, severity levels, and scan history.
Technical Architecture and Implementation
Backend Technology Stack
The backend is built on Django 4.2, a high-level Python web framework that encourages rapid development and clean design. Django provides built-in security features including protection against SQL injection, cross-site scripting, cross-site request forgery, and clickjacking. The project demonstrates advanced Django concepts including custom user models, class-based views, model relationships, and middleware.
Asynchronous Task Processing
Celery is integrated for handling long-running scanning tasks asynchronously. This prevents web requests from timing out and allows multiple scans to run concurrently. Redis serves as the message broker, enabling efficient task distribution and result caching. This architecture demonstrates understanding of distributed systems and asynchronous programming.
Security Scanning Engine
The scanning engine leverages python-nmap, a Python wrapper for the industry-standard Nmap security scanner. Custom scanning logic is implemented to parse Nmap XML output, extract relevant information, and store structured data in the database. Additional HTTP-based scanning uses the requests library to detect web application vulnerabilities, complementing our phishing website detection system.
Database Design
The application uses a relational database with properly normalized tables for users, scans, targets, vulnerabilities, and reports. The schema supports complex queries for filtering, sorting, and analyzing vulnerability data. PostgreSQL is recommended for production, while SQLite works for development and demonstration purposes.
Real-World Applications
Network Security Auditing
Organizations can use this platform to conduct regular security assessments of their network infrastructure, identifying vulnerabilities before malicious actors exploit them.
Penetration Testing Projects
Security professionals can leverage the platform as a foundation for penetration testing engagements, customizing scanning modules for specific client requirements.
Compliance and Governance
The comprehensive reporting and audit logging features support compliance with security standards like PCI DSS, HIPAA, and ISO 27001, which require regular vulnerability assessments.
Educational and Training Purposes
Academic institutions can use the platform to teach network security concepts, demonstrating how vulnerabilities are discovered and documented in professional security assessments.
Security Operations Centers
The platform can be integrated into SOC workflows for continuous monitoring and vulnerability management across enterprise networks.
Learning Outcomes for Students
By working with this final year project, students will gain practical experience in:
- Full-stack web application development using Django framework
- Implementing role-based access control and authentication systems
- Working with asynchronous task processing and message queues
- Integrating third-party security tools and APIs
- Database design and optimization for security applications
- Generating professional PDF reports with ReportLab
- Building responsive web interfaces with Bootstrap and JavaScript
- Understanding network security concepts and vulnerability assessment methodologies
- Implementing audit logging and compliance features
- Deploying and configuring complex web applications
Project Customization Options
The platform is designed to be extensible and can be customized with additional features such as:
- Integration with additional vulnerability scanners like OpenVAS or Nikto
- Automated remediation suggestions using machine learning
- Scheduled recurring scans with email notifications
- REST API for integration with third-party tools
- Advanced visualization dashboards with D3.js
- Export to security orchestration platforms like SIEM systems
- Custom vulnerability plugin development framework
Documentation and Support Included
When you purchase this final year project from CodeAj Marketplace, you receive:
- Complete source code with detailed comments
- Comprehensive installation and setup documentation
- Pre-built project report with problem statement, objectives, methodology, and results
- Professional PowerPoint presentation for project defense
- Database schema diagrams and ER models
- System architecture documentation
- User manual with screenshots
- Testing documentation with test cases
- Video tutorials for project setup and demonstration
Why Choose This Project for Your Final Year
This network vulnerability testing platform stands out as a final year project because it addresses real-world cybersecurity challenges while demonstrating advanced technical skills. The project scope is substantial enough to impress evaluation committees while being manageable within academic timelines. The combination of web development, security tools, and professional reporting makes this an excellent choice for computer science and information security students.
The project documentation is thorough, making it easy to understand the codebase, set up the development environment, and explain the technical implementation during your viva or project defense. With cybersecurity being one of the fastest-growing fields, this project showcases skills that are highly valued by employers.
Perfect for Multiple Specializations
This project is suitable for final year students in:
- Computer Science and Engineering
- Information Technology
- Cybersecurity and Information Assurance
- Network Engineering
- Software Engineering
Get Started Today
Purchase this complete final year project package from CodeAj Marketplace and receive immediate access to all source code, documentation, and support materials. Our team is available to help with project setup, code explanations, and customization requirements to ensure your final year project is a success.
With this ready-made final year project, you save months of development time while gaining a professional-quality application that demonstrates industry-relevant skills in web development and cybersecurity. Explore our other cyber security projects to find additional options that match your interests.
Extra Add-Ons Available – Elevate Your Project
Add any of these professional upgrades to save time and impress your evaluators.
Project Setup
We'll install and configure the project on your PC via remote session (Google Meet, Zoom, or AnyDesk).
Source Code Explanation
1-hour live session to explain logic, flow, database design, and key features.
Want to know exactly how the setup works? Review our detailed step-by-step process before scheduling your session.
₹999
Custom Documents (College-Tailored)
- Custom Project Report: ₹1,200
- Custom Research Paper: ₹1000
- Custom PPT: ₹500
Fully customized to match your college format, guidelines, and submission standards.
Project Modification
Need feature changes, UI updates, or new features added?
Charges vary based on complexity.
We'll review your request and provide a clear quote before starting work.

